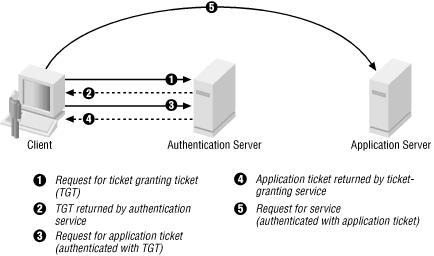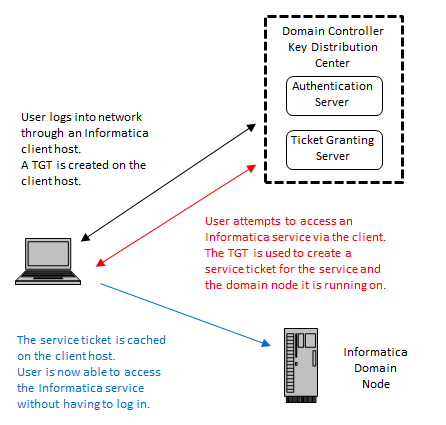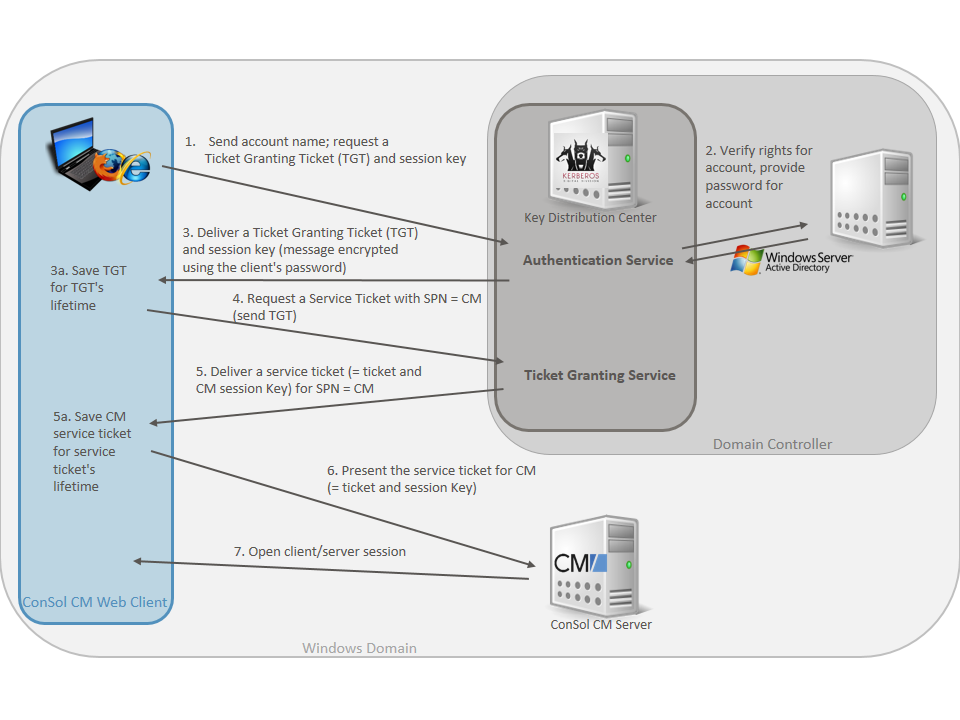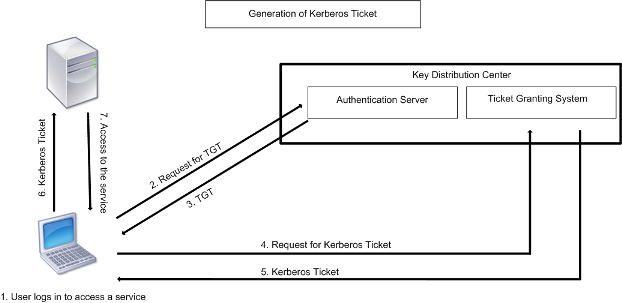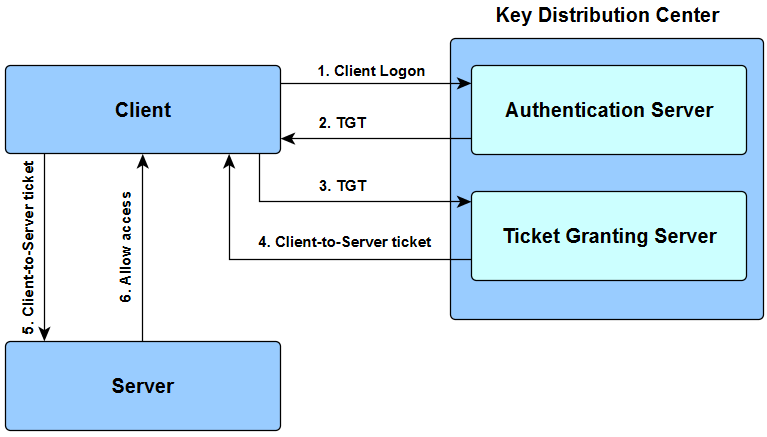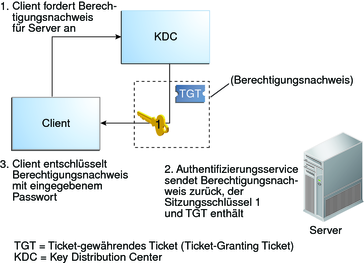
Obtention de l'accès à un service à l'aide de Kerberos - Guide d'administration système : Services de sécurité
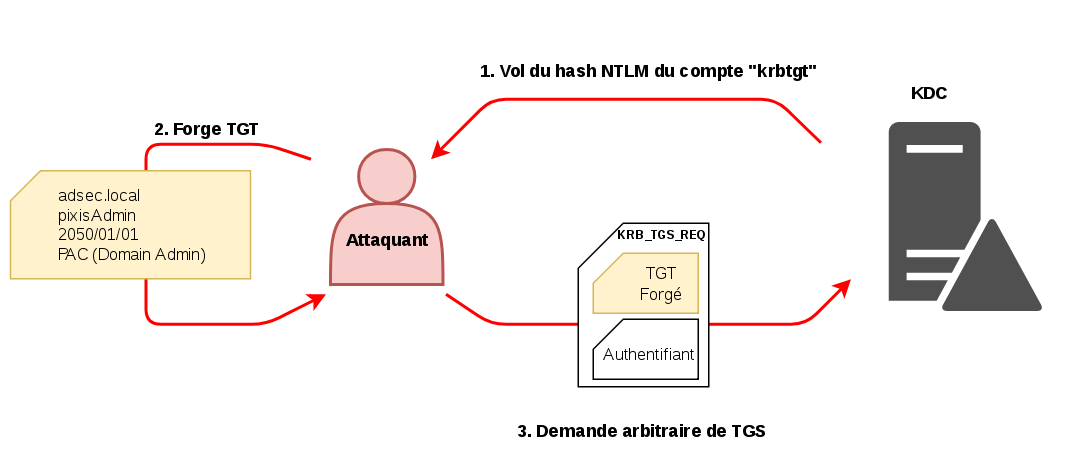
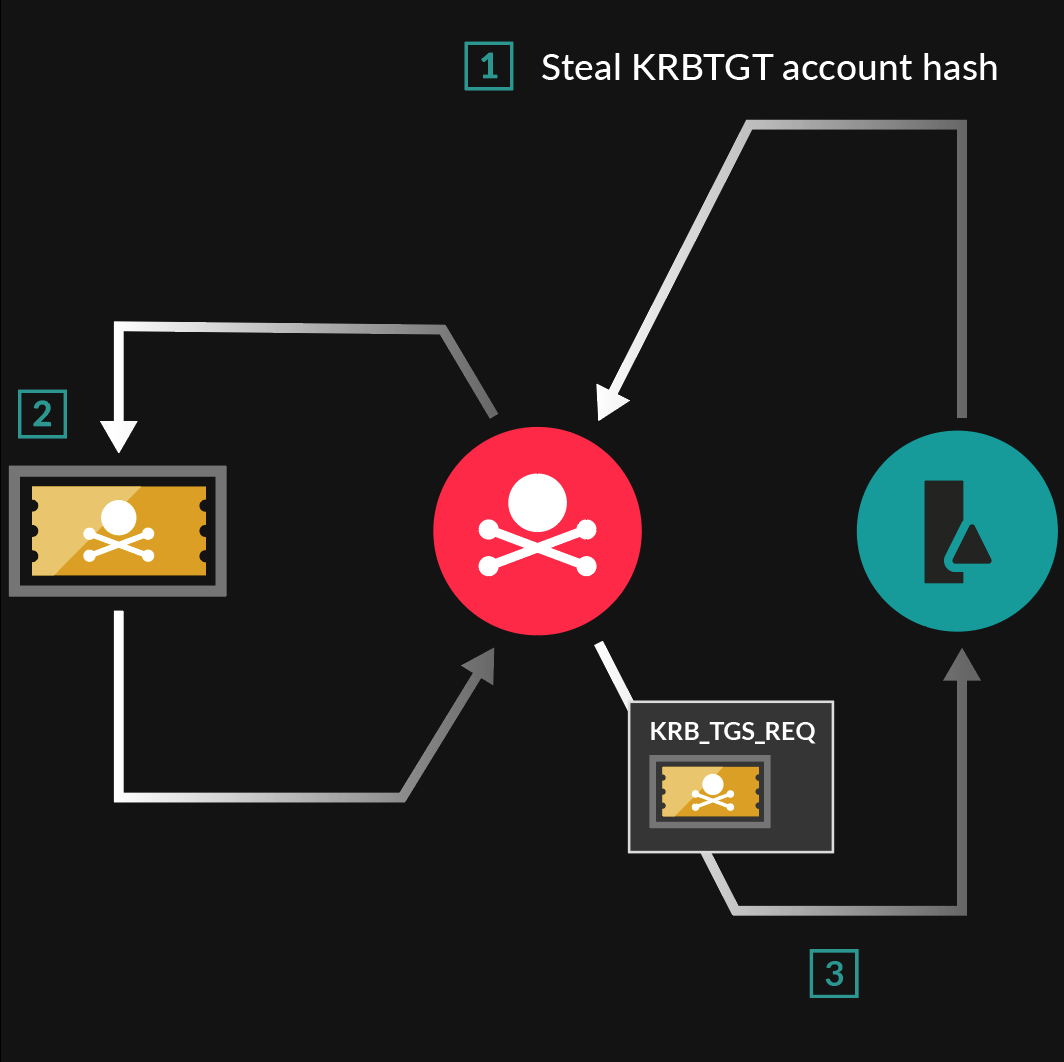
SANS Digital Forensics and Incident Response Blog | Kerberos in the Crosshairs: Golden Tickets, Silver Tickets, MITM, and More | SANS Institute
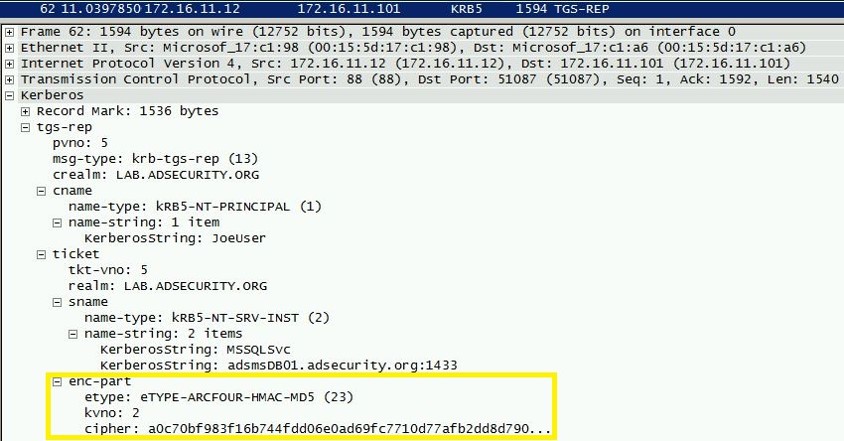
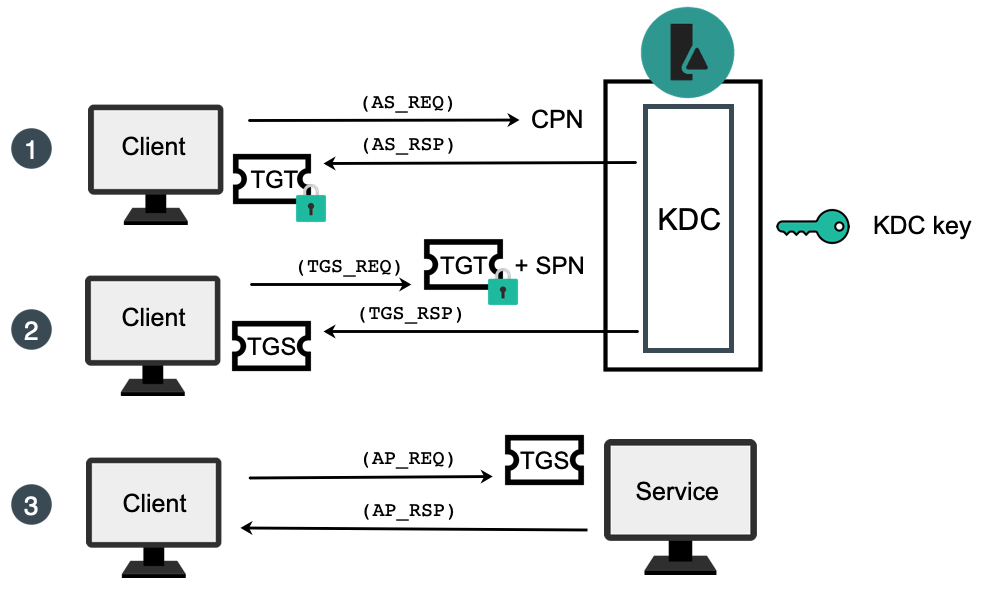
Cracking Kerberos TGS Tickets Using Kerberoast – Exploiting Kerberos to Compromise the Active Directory Domain » Active Directory Security
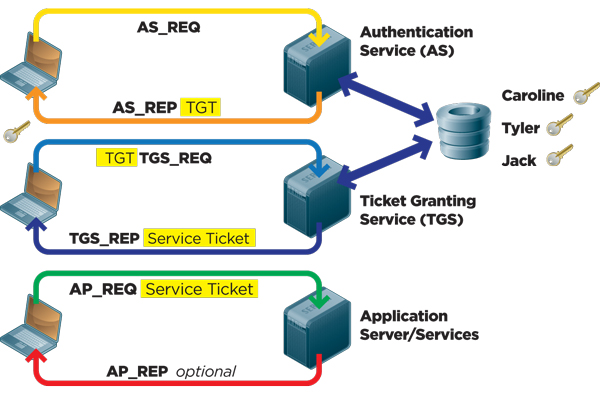
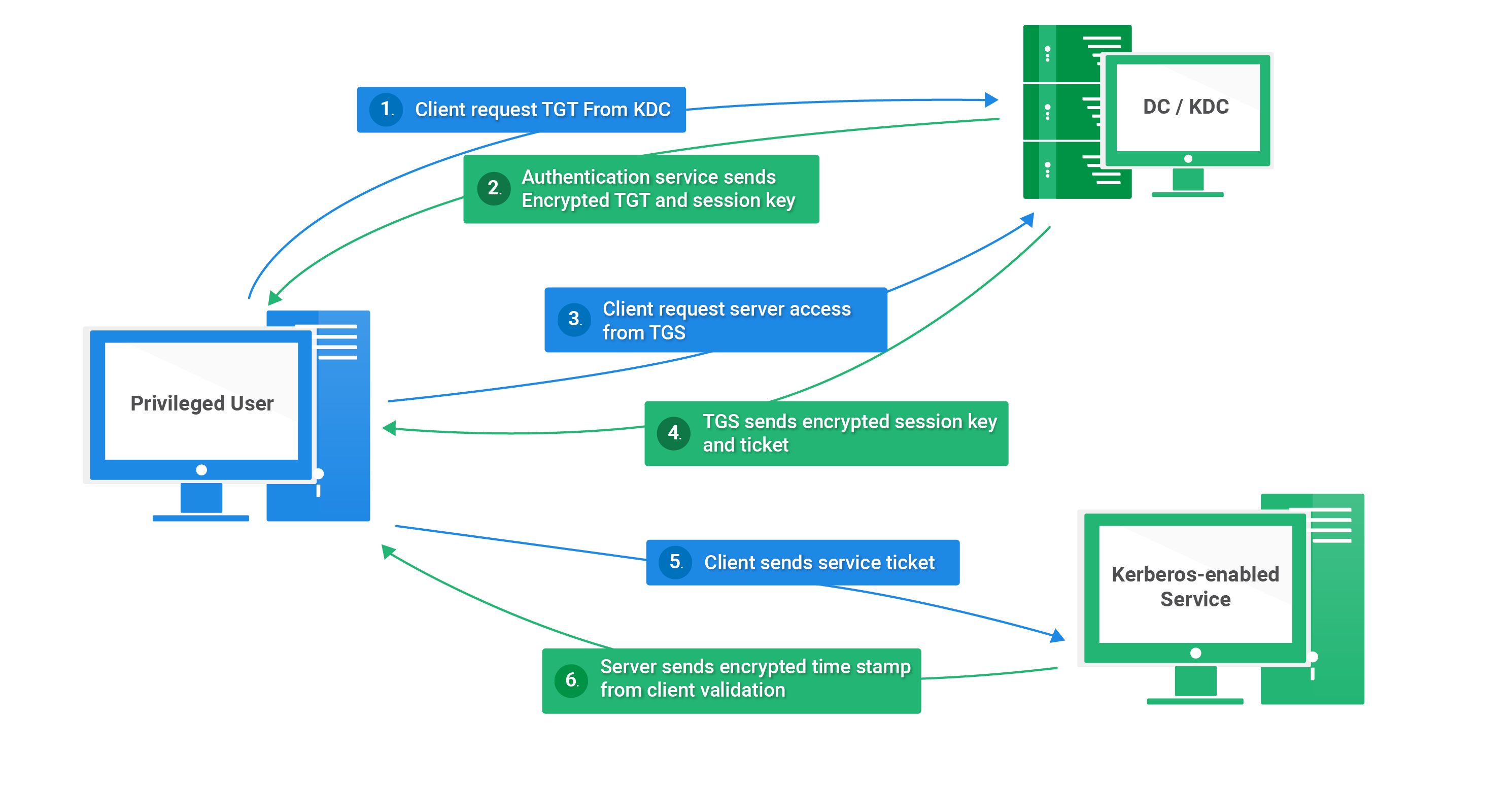
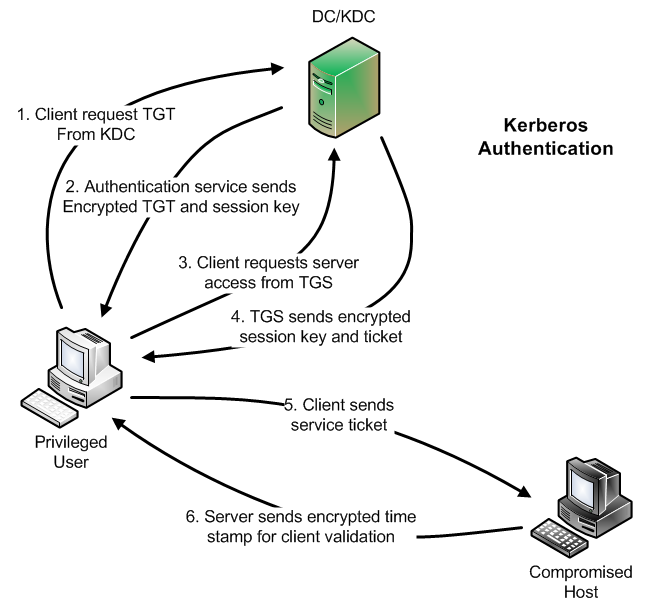
Kerberos Authentication 101: Understanding the Essentials of the Kerberos Security Protocol -- Redmondmag.com
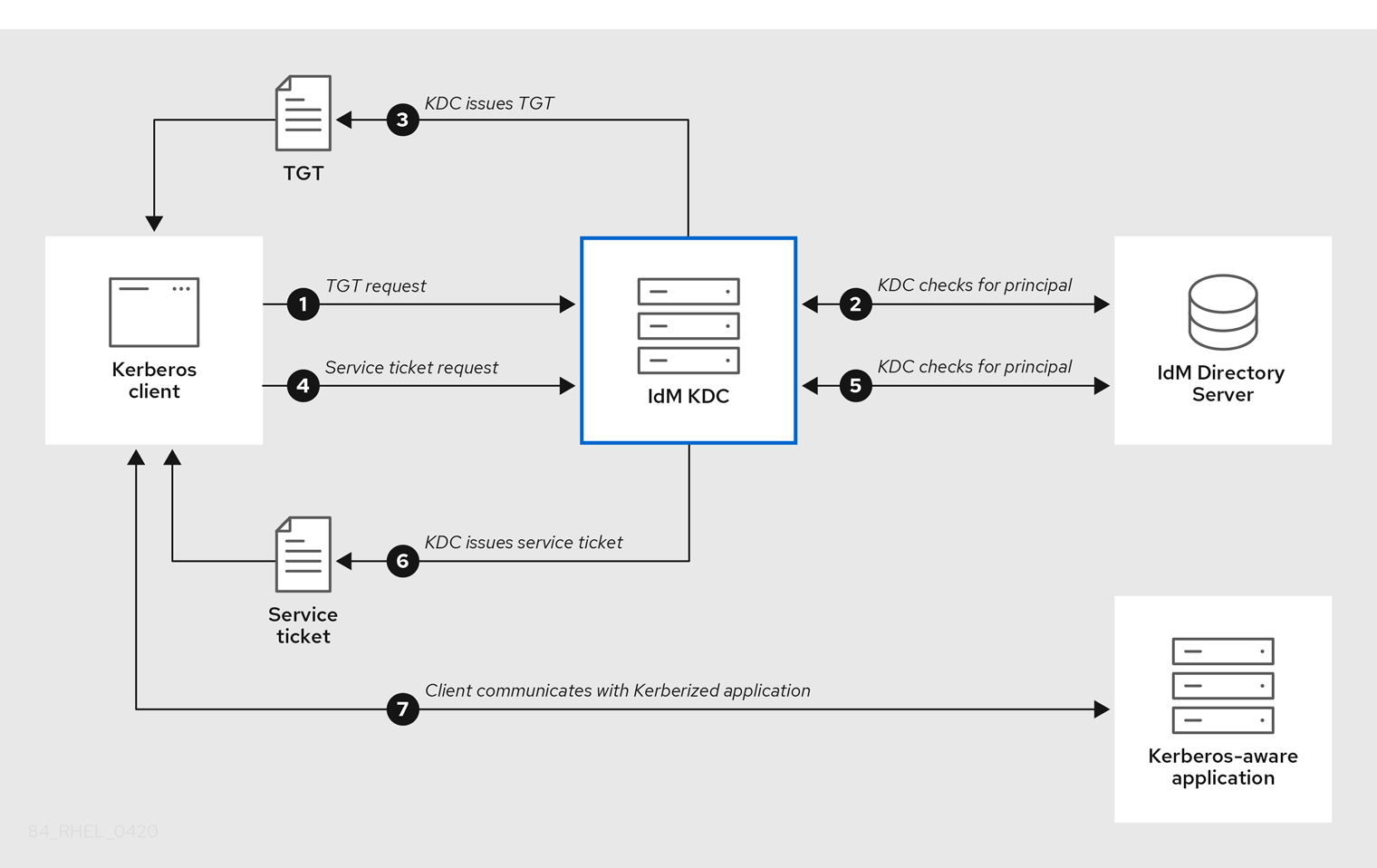
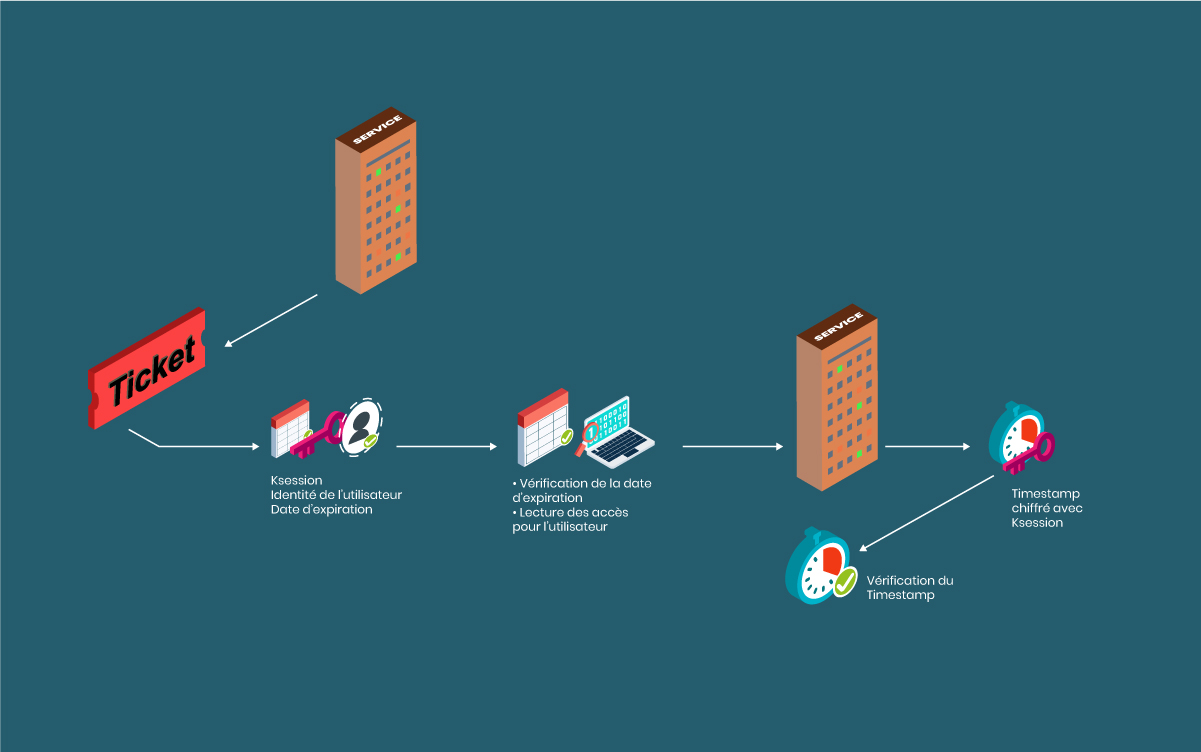
Chapitre 13. Gestion des politiques de tickets Kerberos Red Hat Enterprise Linux 9 | Red Hat Customer Portal